Best Practices for Server Security
Maintaining a secure server is essential to protect your players, resources, and data from potential threats. Follow these best practices to secure your FiveM server.
Step 1: Implement Whitelisting
-
Use a whitelisting system to control who can access your server:
- Many scripts available in The A Team store support whitelisting functionality.
- Alternatively, configure a database-driven whitelist using SQL.
-
Regularly update the whitelist to include or remove players as necessary.
Step 2: Secure Server Configuration Files
-
Restrict access to critical configuration files like
server.cfg:- Ensure only trusted administrators have access.
- Store sensitive data (e.g., database credentials) in an environment file (
.env) instead of directly inserver.cfg.
-
Use encryption for sensitive information.
Step 3: Configure Anti-Crash and DDoS Protection
-
Add these critical security settings to your
server.cfgto protect against various attack vectors:# Layer 7 DDoS Protection and Anti-Crash Settings set sv_requestParanoia 3 # Blocks L7 DDoS attacks by limiting HTTP requests set sv_endpointprivacy true # Enhances endpoint security set sv_forceIndirectListing true # Forces indirect server listing set sv_useDirectListing true # Works with indirect listing for enhanced protection # Authentication Protection set sv_authMinTrust 4 # Higher trust requirement for identity verification set sv_authMaxVariance 5 # Controls identity change probability -
These settings provide multiple layers of protection:
- L7 DDoS Protection:
sv_requestParanoiablocks HTTP-based attacks by limiting access to server endpoints - Anti-Crash Measures: The combination of endpoint privacy and listing settings helps prevent common crash attempts
- Authentication Security: Stricter identity verification prevents spoofing attacks
- L7 DDoS Protection:
-
Detailed Parameter Information:
-
sv_requestParanoia:
- Helps counter proxy-based HTTP floods
- Values 2 and above will return “Nope” for info.json, dynamic.json and players.json endpoints
- Default: 0
- More info: FiveM Documentation
-
sv_authMinTrust:
- Defines how unlikely it is for a user’s identity to be spoofed
- Range: 1-5 (1 being least trustworthy, 5 being most trustworthy)
- Level 5 indicates external three-way authentication
- Default: 1
-
sv_authMaxVariance:
- Determines likelihood of user ID changes for providers (steam, ip, license)
- Range: 1-5 (1 being least likely to change, 5 being most likely)
- Default: 5
-
-
Important Notes:
-
With
sv_requestParanoia 3, the/players.jsonendpoint will return “Nope” after first access: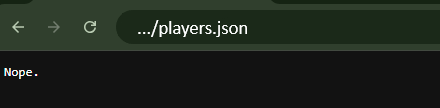
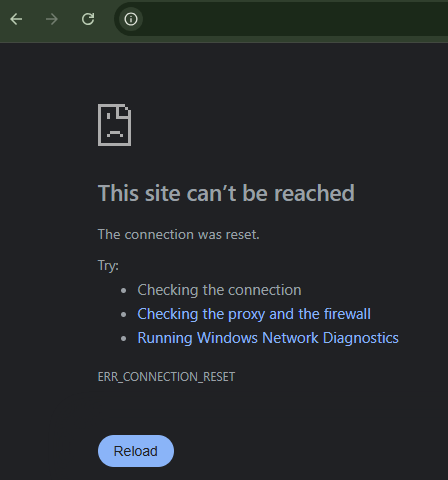
Subsequent attempts will be blocked for several minutes:
-
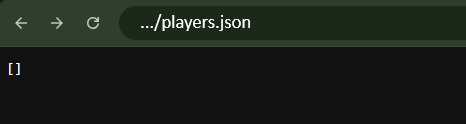
For comparison, an unprotected server response looks like this:
-
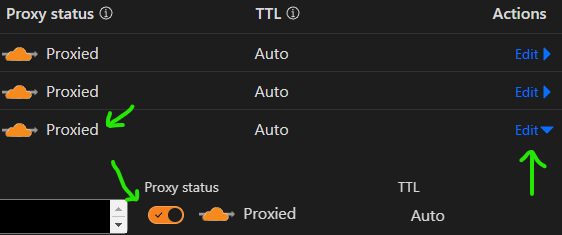
If using Cloudflare or other proxies, be aware these settings may affect proxy functionality:
-
You may notice this warning in your txAdmin console which you can safely ignore:
This is part of FiveM’s security improvements. For more details, see the official announcement.
-
Regular monitoring of server logs is essential to ensure these protections work effectively
-
Step 4: Enable Resource Integrity
-
Add resource integrity checks to prevent unauthorized modifications:
- Define proper file dependencies in resources
fxmanifest.lua. - Regularly verify that no files have been altered without your knowledge.
- Define proper file dependencies in resources
-
Monitor resources with the FiveM
resmontool:resmon 1
Step 5: Monitor Server Logs
-
Regularly review server logs to detect suspicious activity:
- Look for unusual player actions or failed connection attempts.
- Track errors and warnings that might indicate vulnerabilities.
-
Use tools like txAdmin to monitor logs efficiently.
Step 6: Update Resources and Server Software
-
Keep FiveM server artifacts updated to the latest version:
- Download updates from the official FiveM site.
- Restart your server to apply updates.
-
Update purchased scripts and resources from The A Team store to their latest versions.
Step 7: Limit Admin Access
- Assign admin roles sparingly to trusted individuals only.
- Use role-based permissions to restrict access to sensitive commands or features.
Step 8: Protect Against DDoS Attacks
- Use a hosting provider that offers DDoS protection.
- Monitor network traffic for unusual spikes.
Step 9: Backup Regularly
- Schedule regular backups of your server files and database.
- Store backups in a secure, off-site location to ensure recovery in case of data loss.
Securing your server requires vigilance and proactive measures. By following these best practices, you can safeguard your FiveM server and provide a safe environment for your community.